For businesses in Charlottesville and Fredericksburg that are seeking to secure federal contracts, they must comply with the Cybersecurity Maturity Model Certification (CMMC). A common need that a CSP can provide is the ability to reduce scope and create an enclaved environment that helps achieve compliance more affordably. But what specifically is a CSP? And why does it matter for handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI)?
This blog aims to explore the importance of CSPs in the CMMC framework, discussing the security standards that must be met. We’ll also explore how our expert IT support in Charlottesville and Fredericksburg can help businesses navigate CMMC compliance with ease.
What Is a Cloud Service Provider?
A Cloud Service Provider (CSP) is a company that offers a range of cloud computing services, such as storage, processing power, and software applications, over the internet. CSPs enable businesses and individuals to access and use these resources without needing to invest in and maintain physical hardware and infrastructure. Some well-known CSPs include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Why CSPs Can Be Critical for CMMC Compliance
At times, utilizing a CSP can be a great fit for leveraging some technical advantages of cloud services, improving the efficiency of your Information Systems. It is important to know, though, that when it comes to storing, processing, or transmitting CUI data, you can only work with CSPs that are either FedRAMP Moderate Authorized or have met FedRAMP Moderate Equivalency.
FedRAMP Moderate Authorized refers to a certification level within the Federal Risk and Authorization Management Program (FedRAMP). This certification ensures that a Cloud Service Provider (CSP) meets stringent security requirements for handling sensitive but unclassified data. The “Moderate” impact level is designed for systems where the loss of confidentiality, integrity, or availability would result in serious adverse effects on an organization’s operations, assets, or individuals.
To achieve FedRAMP Moderate Authorization, a CSP must undergo a rigorous security assessment process, including continuous monitoring and periodic reassessments, to ensure ongoing compliance with federal security standards.
FedRAMP Moderate Equivalent refers to a designation for Cloud Service Providers (also referred to as Cloud Service Offerings, CSOs) that meet the security requirements of the FedRAMP Moderate baseline but have not gone through the formal FedRAMP authorization process. To achieve this equivalency, they must comply 100% with the latest FedRAMP Moderate security control baseline through an assessment conducted by a FedRAMP-recognized Third Party Assessment Organization (3PAO) and provide comprehensive supporting documentation (see https://www.fedramp.gov/ and https://marketplace.fedramp.gov/ for more information).
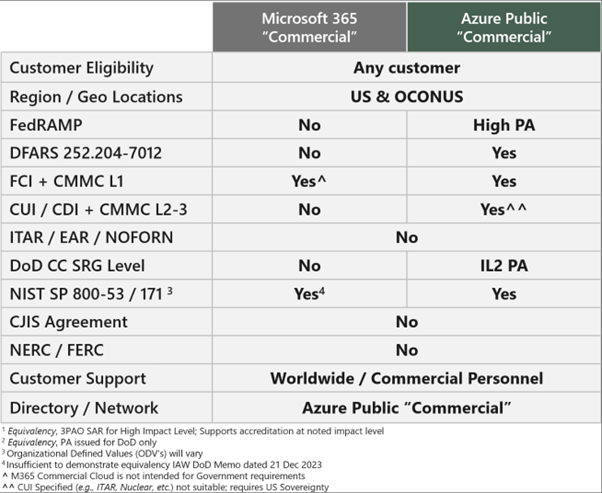
For government contractors not interacting with CUI, they still need to utilize a CSP that can meet CMMC Level 1 controls. The Microsoft Commercial platform can be configured to do this and is used frequently despite some confusion with all the offerings that M365 brings to the table. See table below and reference HERE.
For businesses handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), it’s essential to have robust, secure, and compliant cloud solutions to keep them protected against evolving cyber threats.
This is where a CSP can be configured to maintain data security, and under CMMC 2.0, organizations must work with FedRAMP Moderate or higher-authorized CSPs to ensure they meet compliance requirements.
Data Security: Protecting FCI and CUI from Cyber Threats
Making sure that your data is kept safe should be a priority for every business. Cyber threats such as ransomware, insider attacks, and data leaks are growing concerns for businesses handling government data. Data security is essential for compliance, particularly CMMC. A CMMC-compliant CSP offers:
- Secure Cloud Storage: Encrypts data at rest and in transit, reducing the risk of breaches.
- Strict Access Controls: Uses multi-factor authentication (MFA) and role-based access restrictions to limit unauthorized access.
- Continuous Monitoring & Threat Detection: Identifies and mitigates security threats before they impact operations.
Choosing the Right CSP: What to Look For
When choosing a cloud provider for CMMC, it’s important to select carefully, as not all cloud providers meet CMMC and FedRAMP standards. When evaluating a CSP for CMMC compliance, look for:
- FedRAMP Moderate or FedRAMP Moderate Equivalency: Essential for handling FCI and CUI securely.
- Government-Approved Cloud Environments: Platforms like Microsoft Government Community Cloud (GCC) High, AWS GovCloud, and Google Cloud Assured Workloads are specifically designed for CMMC compliance. However, there are many more options, sometimes more affordable, that meet requirements for CUI and FCI.
- End-to-End Encryption & Compliance Support: Ensures data security while helping businesses prepare for CMMC audits.
Infinity Technologies: Supporting CMMC Compliance
Achieving and maintaining compliance can be a challenge. That’s why, at Infinity Technologies, we help businesses navigate the complexities of CMMC compliance. Our IT support and managed services in Charlottesville and Fredericksburg enable businesses to secure their IT infrastructure and ensure compliance with federal cybersecurity standards. We provide:
- CMMC Readiness Assessments: Identify security gaps and ensure compliance readiness.
- Secure Cloud Solutions: Implement FedRAMP-compliant cloud services tailored to your business needs.
- 24/7 IT Monitoring: Keep your systems secure and operational around the clock.
- Incident Response & Cybersecurity Management: Mitigate risks and prevent data breaches.
Book a 1:1 Consultation Today
Choosing the right CSP is a critical step in achieving CMMC compliance. With increasing cybersecurity threats and evolving government regulations, businesses in Charlottesville and Fredericksburg must ensure they are using secure, compliant cloud services.
Contact us today to book your 1:1 meeting and take the next step toward securing your federal contracts!



